Playing ‘pass the grenade’?
Are you playing ‘pass the grenade’ with your business? Is your entire industry doing it? And if so, what can you do to defuse the metaphoric grenade?
What’s the ‘grenade’? Well, it’s kinda like a hot-potato – except that you’ll know when you have a hot-potato, because it burns everyone’s fingers somewhat in passing, whereas a grenade feels perfectly safe and ordinary and unimportant until it blows up in your face…

In this type of context, the grenade is a graphic metaphor for the eventuation of a kurtosis-risk: a seeming low-probability risk that, when it eventuates, more than wipes out all of the gains previously made by ignoring that risk. In business, the most common kind of ‘grenade’ is anything which undermines trust of that business, whether from customers, suppliers, the market in general, investors, or other seemingly ‘non-involved’ stakeholders further out in the shared-enterprise. Some of the more infamous examples include:
- so-called ‘customer-service’ whose design, either by default or by intent, denies those who need that service from receiving it
- Kafkaesque policies and procedures that make it all but impossible to obtain service or self-service
- ‘prank calls’ and other abusive practices, aimed at other employees, customers or ‘outsiders’
- abuses and misuses of monopoly position or status
- misleading or dubious sales-practices such as unneeded or concealed ‘payment protection insurance‘
- carelessness with or cavalier attitudes to customer-data, privacy, or outright spying
‘Pass the grenade’ occurs when the risk is ignored because it seems to be (very) low-probability, but is then increased through creation of many more instances of the same risk. Each individual instance remains a low-probability risk – such as when people become inured to poor-quality service – but the collective risk that some customer will finally scream “I’m not going to take it any more!” and do something fairly lethal about it increases with each instance. The result is what looks like a low-probability risk that is actually increasing every day – and yet it still remains all but impossible to identify which instance will be the one that finally explodes.
The risk increases even further, and grows in scale and potential impact, when an entire industry or culture joins in the game – hence ‘pass the grenade’. Often there is awareness that the risk is real, but hiding in denial, or in the hope that it will only be someone else – some other company, some other player – who’s holding the grenade when it finally explodes. However, if the explosion is sufficiently severe to take down an entire industry, that kind of hope isn’t much of a defence…
The only real way to mitigate the risk is to look at the context as a whole, to identify points where trust may be placed at risk, and mitigate those. However, these mitigations often imply apparent costs, especially in the short-term – which means that pressures may be applied to continue to ignore the risks, on grounds of cost. These pressures will come particularly from those so steeped in the certainty-orientation of the Taylorist tradition that they assume that ‘low-risk’ equates to ‘no risk’; and, perhaps even more, from stockholders who stand to gain financially from short-term profits but who are isolated and protected from the risks – or who may even take out an ‘each-way bet’, such that they always ‘win’, regardless of what happens to the company and to everyone else.
[As an aside, note that most current stock-market models and commercial will actively promote such dysfunctional behaviours – such as the concept of the ‘limited-liability company’, in which profits are personal but losses are socialised; or the absence of any time-constraints on stockholding, that isolate stockholders alone from long-term risks or their consequences.]
The most popular way to avoid tackling the risk is by trying to block it or offload it through some form of ‘the law’ – such as by deniability in the small-print of a contract, through monopolies and other privileges obtained by lobbying or outright bribery of legislators, or through supposedly-unchallengeable ‘secret courts’ and suchlike. The blunt reality, though, is that such ‘legal’ tactics do not work – in fact they place the rule of law itself at risk, by damaging trust in the validity or fairness of law as a whole. The core of the issue here, and the risk, revolves around trust: and trust is an emotion – it’s not something that can be mandated by law.
Loss of trust creates non-clients, or at best merely disengaged and unwilling clients. But betrayal of trust creates active anti-clients: people who have what is, to them, clear motivation to bring down the business-model of those who they feel have betrayed them. The motivation may be expressed as action against ‘the betrayers’ – which, with the leverage now provided by social-media, may have far greater impacts than in the past. But the motivation may also be expressed as design of alternate business-models that can bypass or render irrelevant those of ‘the betrayers’ – including bypassing apparently-unbreakable monopolies, such as micro-mills did to the steel-industry, or torrent-streams did to much of the media-industry. The same can also apply to supposedly-essential institutions such as the university-system or the justice-system, and even to the concept of ‘government’ itself – a fact which is starting to sink home even in supposed ‘democratic’ countries, let alone elsewhere…
Trying to pretend that the problem doesn’t exist, or suppress any acknowledgement of the problem, or try to force it always to be ‘Somebody Else’s Problem’, doesn’t make the risk go away: all it does is merely make it worse, and makes a more damaging explosion even more likely. Whichever way we play it, ‘pass the grenade’ is not a wise game to play…
Implications for enterprise-architecture
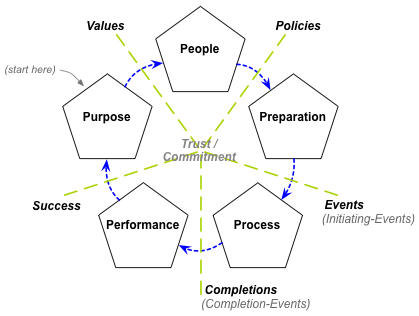
To my view, perhaps the key role of enterprise-architecture is to ensure that, across the whole of the scope in context, things work better when they work together, on purpose. In turn, trust is perhaps the key lubricant for ‘things working together’: without trust, everything grinds to a halt. Hence we can visualise trust – and its active counterpart of commitment – as being the centrepoint around which everything in the enterprise would revolve:
In this sense, management and maintenance of trust is a fundamental concern for all forms of enterprise-architecture. The relevant forms of trust may vary somewhat according to the scope of the enterprise-architecture: in IT-only enterprise-architectures, for example, we might see trust primarily in terms of privacy, security and reliability. But whatever the context and scope, the principle remains the same: trust is at the very centre of the enterprise – and without it, nothing works.
To mitigate risks of damage to trust, we might need some or all of the following:
— Do customer-journey mapping and customer-experience mapping to identify any trust-related issues – preferably iterative multiple-journey mapping, as trust typically rises or falls around repeat-business or full-completions of journeys (from the customer’s perspective, not just the organisation’s).
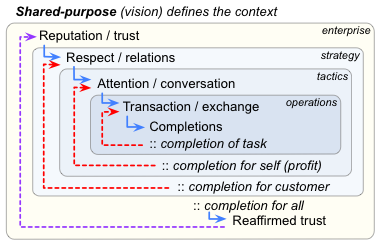
— Do service-cycle mapping, as per the Service Cycle in the Enterprise Canvas framework:
The key concern here is that trust is only reaffirmed and maintained on completion of the whole cycle, including to the satisfaction of those in the ‘outer’ (non-active) regions of the shared-enterprise – not merely the transaction-oriented subset that occurs in the more-visible middle-stages of the cycle:
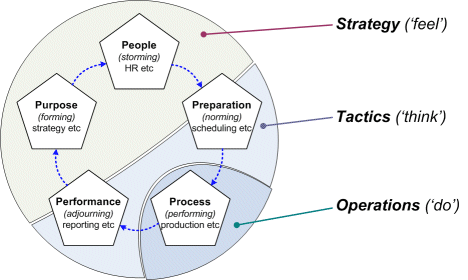
Similarly – and especially over the longer-term – the service-cycles need to fully encompass the strategic linkage to the shared-enterprise, as well as the tactical and operational concerns that are the more visible concern for the organisation:
In particular, watch for any tendency in business-models, service-designs or systems-operations etc to fall into the classic ‘quick-profit failure-cycle’, where loss of connection back to the more ‘feeling’-oriented strategic realms also leads directly to loss of trust:
Trust is fundamental here: and the ‘quick-profit failure-cycle’ is a long-proven anti-pattern for destroying trust in a business. Despite many common business-delusions, the organisation does not ‘possess’ the shared-enterprise, and loss of trust will lead to ejection from the shared-enterprise. Or, to put it in terms that even the most money-obsessed of business-folk would understand, loss of trust = loss of business = loss of all possibility for profit.
Mitigation of this (very real) risk provides the business-reason for enterprise-architectures that focus on whole-of-context concerns such as trust – rather than, say, the kind of domain-specific ‘efficiency’ focus more typical of classic IT-oriented enterprise-architectures.
Hence, in addition to customer-experience mapping and service-cycle mapping:
— Do trust-mapping, to identify potential sources, sinks and leaks for trust. Probably the most useful approach is to apply conventional asset-mapping, regarding ‘trust in the organisation’ as an organisational asset. Once we do this, we can apply much the same kind of CRUD analysis as for other types of assets:
- what processes and activities inside and beyond the organisation create trust? – for example, relationship-building, marketing, value-proposition, values
- what processes and activities inside and beyond the organisation read trust? – for example, sales, marketing
- what processes and activities inside and beyond the organisation update trust? – for example, product-usage, post-service-delivery follow-up, customer-service
- what processes, activities or attributes inside and beyond the organisation could destroy trust? – for example, mismatch of expectations, perceived non-delivery on or betrayal of perceived promises
Note that these processes, activities and risks may occur anywhere: in IT-architectures, for example, they can often occur in the gaps between IT-systems, such as where a crude copy-and-paste is required as a kludge to compensate for poor inter-system integration.
Although the mapping and analysis are much the same as for data-assets, it’s essential to remember that trust is a fundamentally-different type of asset: technically, an aspirational-type asset that exists between a human-entity and virtual-entity (rather than as a virtual-entity in its own right, as for data) and is non-alienable and non-possessable (unlike for physical-assets or – nominally – for financial-assets).
Important: remember that whilst ‘information about trust’ may be relatively-easy to model, it’s not the same as trust itself! The latter is what we need to track – and ‘information about trust’ is only a means to that end. Don’t mix them up!
Anything which damages trust – and especially anything that does so in a way that is seemingly-easy to ignore in the short-term – is a potential ‘grenade’: tracking these down, and mitigating their risks, should be a core survival-concern for the organisation and its architectures.


0 Comments on “Playing ‘pass the grenade’?”